Adobe Acrobat Reader X is not working on some computers, or on some user profiles. We don't know the cause, as it appears to be intermittent. It seems to have something to do with the profile redirection settings.
Some of the issues include "out of memory" errors when trying to print and failure to launch the Acrobat Reader web browser plugin in Internet Explorer.
The workaround for getting PDFs to appear from a web browser is to right-click on the link and save the document to your home folder, then double-click on the document to open it.
If you you encounter this problem, please submit a helpdesk ticket at http://helpdesk.oregonsd.net and be sure to include your building, room number, and computer FA #.
Thursday, December 16, 2010
Wednesday, December 15, 2010
Public web site scheduled outage
Our public website will be undergoing maintenance on Saturday, which will involve some outages. SchoolWorld will be performing server maintenance on Saturday, December 18, 2010 from 8:00 AM - 12:00 PM ET. While there will not be a complete outage during the maintenance window, connectivity will be sporadic during the required server reboots. We appreciate your understanding.
Tuesday, November 23, 2010
Internet access restored, and scheduled outage tomorrow is cancelled
Internet access has been restored, many thanks to Jim and Chen from Wiscnet! All services are now operating normally. In the course of troubleshooting, we went ahead and migrated the circuits to a load-balancing configuration ahead of schedule, so tomorrow morning's scheduled Internet outage has been canceled.
Internet service problems
The district's Internet connection has had intermittent unreliability today. It is still unresolved, though we are working with WiscNet technicians to solve the problem. The issues are making it difficult for staff to check email, and Internet access from inside the district is largely unavailable. We will continue working tonight to get it resolved, and tomorrow's schedule outage from 8-9 AM is still on schedule, though we may need to use it to continue to resolve this issue.
Thanks for your patience. Hopefully you are cooking Turkey, not checking email.
Thanks for your patience. Hopefully you are cooking Turkey, not checking email.
Thursday, November 18, 2010
Scheduled Internet Outage 11/24 8:00 - 8:30 AM
There will be a scheduled Internet outage from 8:00 - 9:00 AM on Wednesday, November 24, so that we can test a newly installed Internet connection circuit with BCN. This is in preparation to set up a redundant Internet link so we can maintain connectivity in the event of an outage.
There will likely be multiple short interruptions during the outage window. You can feel free to try to connect, but be aware that interruptions are likely, so be sure to save often!
There will likely be multiple short interruptions during the outage window. You can feel free to try to connect, but be aware that interruptions are likely, so be sure to save often!
New services coming to Google Apps!
Important changes are coming to your OSD (@oregonsd.net) Google Apps account. Your account will soon be converted and start working more like a full Google Account.
What this change will mean for you:
What this change will mean for you:
- Access to many more Google products. You'll soon be able to use many more Google services with your oregonsd.net account, such as Blogger, Picasa, Google Reader, and many more.
- New sign in option. You will be able to sign in to Google services from the regular sign-in pages (like http://mail.google.com). Your username is your full oregonsd.net email address.
- For more information, we encourage you to review the Transition Checklist. The Help Center also has answers to many common questions (note that you won't be able to view the full Help Center until you've been transitioned).
- If you have other questions, please contact Jon (jst at oregonsd dot net) or the helpdesk.
Tuesday, November 16, 2010
Email error messages when sending to other staff
Some staff have reported that mail they sent to other staff this morning has been returned to them with an error message 550. After extensive investigation, here's my best guess of what is happening:
When Postini sees a spam attack, it blocks spam messages and sends back "ERROR 550 Mailbox not available" to the spam source to fool it into thinking that the mailbox doesn't exist.
Postini found a spam attack that originated from a Google server. It put a block in place. Email messages from our staff to other staff which happened to originate from the same IP address as the spam attack were blocked, and the 550 error was sent back to the original sender.
That's my guess. To test it, I changed the bounceback message in Postini to 571 "Spam source blocked." (The block is no longer in place, but could start up again.)
If you get a bounceback error message when you try to send a message to other staff, please do the following:
Thanks!
When Postini sees a spam attack, it blocks spam messages and sends back "ERROR 550 Mailbox not available" to the spam source to fool it into thinking that the mailbox doesn't exist.
Postini found a spam attack that originated from a Google server. It put a block in place. Email messages from our staff to other staff which happened to originate from the same IP address as the spam attack were blocked, and the 550 error was sent back to the original sender.
That's my guess. To test it, I changed the bounceback message in Postini to 571 "Spam source blocked." (The block is no longer in place, but could start up again.)
If you get a bounceback error message when you try to send a message to other staff, please do the following:
Thanks!
Friday, November 12, 2010
Planned Internet outage Wednesday, 11/17, 4:00 - 4:30 PM
The District's Internet connectivity will be interrupted on Wednesday, November 17 between 4:00 and 4:30 PM to perform testing on our Internet router in preparation for installation of a redundant backup system.
If you attempt to use Internet resources during this time, you may experience an unexpected disconnection, which could lead to data loss. Please avoid using the Internet during this time.
If you attempt to use Internet resources during this time, you may experience an unexpected disconnection, which could lead to data loss. Please avoid using the Internet during this time.
Friday, November 5, 2010
Internet access is down...
UPDATE: Internet access has been restored.
>>>
Network: WiscNet
Type: Unplanned Outage
Location: Wisconsin
Ticket Number: 178461
Party:
Start Time: 11/5/2010 11:54 CDT
End Time: Unknown
Description: Widespread Charter Outage
Engineers:
Reporters:
Affected:
Charter Customers
Notices:
Maria Accuardi @ 2010-11-05 12:22:04
Multiple Charter sites around the state lost connectivity at 1154.
Network Engineers are currently looking into the issue.
>>>
Internet access is down due to a wide spread charter issue in the Madison area.
>>>
Network: WiscNet
Type: Unplanned Outage
Location: Wisconsin
Ticket Number: 178461
Party:
Start Time: 11/5/2010 11:54 CDT
End Time: Unknown
Description: Widespread Charter Outage
Engineers:
Reporters:
Affected:
Charter Customers
Notices:
Maria Accuardi @ 2010-11-05 12:22:04
Multiple Charter sites around the state lost connectivity at 1154.
Network Engineers are currently looking into the issue.
>>>
Internet access is down due to a wide spread charter issue in the Madison area.
Sunday, September 26, 2010
Slow progress
Since school began, 758 helpdesk tickets have been submitted. Of those, 621 have been closed (and yes, I realize that not all closed tickets are really fixed- sometimes we fix a problem, but haven't actually solved the issue).
If you have a helpdesk ticket that has not been solved, I apologize. We have been working at less than full staffing for much of the last month for a variety of reasons, and we are also dealing with many "growing pains" associated with recreating our network operating system, authentication system, software distribution methods, print servers, and data servers. We are learning a whole new operating system, management tools, and methods of operation. The result is that we can't solve problems as quickly as we would like, since we are encountering many of them for the first time.
With such overwhelming demands, we have had to prioritize. I realize that every issue is important, so it feels frustrating to not have your issues resolved in a timely manner. We are taking all factors into account and dealing with many issues that are "behind the scenes" such as creating software installation packages, re-creating print server systems, helping get HVAC servers working again so that heat and AC can work properly, and getting the new website running correctly (which is the #1 request from parents).
We realize this is stressful for you, as it is for us. Thanks for patience and understanding as we try to get everything running as quickly as possible.
If you have a helpdesk ticket that has not been solved, I apologize. We have been working at less than full staffing for much of the last month for a variety of reasons, and we are also dealing with many "growing pains" associated with recreating our network operating system, authentication system, software distribution methods, print servers, and data servers. We are learning a whole new operating system, management tools, and methods of operation. The result is that we can't solve problems as quickly as we would like, since we are encountering many of them for the first time.
With such overwhelming demands, we have had to prioritize. I realize that every issue is important, so it feels frustrating to not have your issues resolved in a timely manner. We are taking all factors into account and dealing with many issues that are "behind the scenes" such as creating software installation packages, re-creating print server systems, helping get HVAC servers working again so that heat and AC can work properly, and getting the new website running correctly (which is the #1 request from parents).
We realize this is stressful for you, as it is for us. Thanks for patience and understanding as we try to get everything running as quickly as possible.
Wednesday, September 15, 2010
Can't find the program you need on your computer? Here's a solution!
Do you ever log in to your computer and look in the Zenworks Application menu, but can't find a program that you should have? Well, we know one reason this might happen, and have a solution.
When you log in, if you see a Zenworks login window, DO NOT CLICK CANCEL! (Yes, we may have told you to click "cancel" before, but it turns out that this is a bad idea.) Instead, LOG IN, using your OSD username and password. It should either work, or you'll get an error message.
If it works, great! If you get an error message, you can either report the computer to the helpdesk, or you can fix it yourself by doing the following steps:
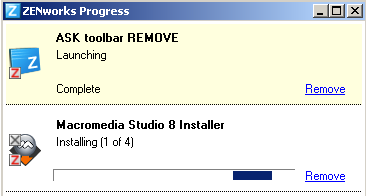
"Okay," you say, "but at least you can see the elevator doors, so you know when the elevator is actually doing something."
Here's a tip: If you want to see if Zenworks is actually installing the application on your computer, you can right-click on the Z icon in the toolbar and select "Show Progress." This will show you what it's doing.
You can also look very carefully at the application icon itself. While it's installing, it has some little green downward arrows on it, indicating "I'm downloading." When it's done, it has a little red Z on it, indicating, quite unintuitively, that it is installed. But really, that's so small, I don't expect anybody to pay much attention to it.
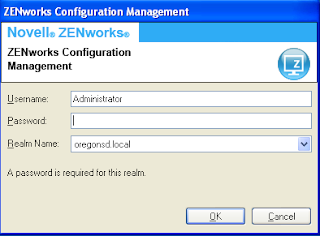 |
| ZENworks login window. Don't click cancel! |
If it works, great! If you get an error message, you can either report the computer to the helpdesk, or you can fix it yourself by doing the following steps:
- Open the E: drive on your computer.
- Delete the file called "register.txt".
- Reboot the computer. It will re-register with the Zenworks server, reboot once on its own, and then you can log in.
- Log in.

"Okay," you say, "but at least you can see the elevator doors, so you know when the elevator is actually doing something."
Here's a tip: If you want to see if Zenworks is actually installing the application on your computer, you can right-click on the Z icon in the toolbar and select "Show Progress." This will show you what it's doing.
Wednesday, September 8, 2010
Don't let your teacher website disappear on Halloween!
Tech alert for all teachers who have a teacher website
Don't let your website disappear on Halloween! On October 31, 2010, the old public website at http://old.oregonsd.org will disappear. If your website is on it, and you want to keep it, you need to move it!
How? Glad you asked. Here are the four basic steps.
Q: Why do we have to do this?
A: We got lots of complaints about our old website, it looked pretty shoddy compared to neighboring districts, and we had a long list of requested features. The old website was declared a "dead end" product by the maker- there was no way to upgrade it and maintain the content, including teacher web sites. We evaluated many options and chose SchoolWorld.
Q: Why did you wait until now to make the change?
A: Well, we had intended to roll out the new website in early July, but we ran into some technical and design issues, so it wasn't completed until early August. We told everybody how to move their content to the new website via email and blog post on August 11. Unfortunately, August is a really horrible time to ask anybody to change things, and we understand that. It wasn't what we intended, but it's how it ended up. To avoid mass panic of websites disappearing in August, we paid for an extension of our old site until October 31.
Q: Why will our old stuff disappear?
A: Our contract with Powercom/CMS4Schools/CESA6 was set to end in August. We purchased an extension to keep it live for another couple months to give everybody time to move their content.
Q: But we just did this a couple years ago- how do we know SchoolWorld won't go away in three years so we have to do this all over again?
A: The old website provider was a small Wisconsin company that changed ownership multiple times. It was selected under extremely short time constraints. SchoolWorld is a national company used by many districts. It constantly updates its services, adding new features, unlike the old website which was declared a "dead end" product by its maker. Therefore, the need to replace SchoolWorld is much less likely.
Q: What if I need help?
A: Our Information Technology Literacy Teachers are available to help!
Any other questions or concerns? Feel free to contact me.
Don't let your website disappear on Halloween! On October 31, 2010, the old public website at http://old.oregonsd.org will disappear. If your website is on it, and you want to keep it, you need to move it!
How? Glad you asked. Here are the four basic steps.
- Choose a new place for your site. You basically have four options, which are explained here.
- Decide if your old stuff is really worth saving, or if you would be better off just starting from scratch. (If you are starting from scratch, skip to step 4.)
- If your old stuff is worth saving/transferring, download it from your old site at http://old.oregonsd.org and save it someplace memorable.
- Upload your content to the new place you chose in step 1.
Q: Why do we have to do this?
A: We got lots of complaints about our old website, it looked pretty shoddy compared to neighboring districts, and we had a long list of requested features. The old website was declared a "dead end" product by the maker- there was no way to upgrade it and maintain the content, including teacher web sites. We evaluated many options and chose SchoolWorld.
Q: Why did you wait until now to make the change?
A: Well, we had intended to roll out the new website in early July, but we ran into some technical and design issues, so it wasn't completed until early August. We told everybody how to move their content to the new website via email and blog post on August 11. Unfortunately, August is a really horrible time to ask anybody to change things, and we understand that. It wasn't what we intended, but it's how it ended up. To avoid mass panic of websites disappearing in August, we paid for an extension of our old site until October 31.
Q: Why will our old stuff disappear?
A: Our contract with Powercom/CMS4Schools/CESA6 was set to end in August. We purchased an extension to keep it live for another couple months to give everybody time to move their content.
Q: But we just did this a couple years ago- how do we know SchoolWorld won't go away in three years so we have to do this all over again?
A: The old website provider was a small Wisconsin company that changed ownership multiple times. It was selected under extremely short time constraints. SchoolWorld is a national company used by many districts. It constantly updates its services, adding new features, unlike the old website which was declared a "dead end" product by its maker. Therefore, the need to replace SchoolWorld is much less likely.
Q: What if I need help?
A: Our Information Technology Literacy Teachers are available to help!
Any other questions or concerns? Feel free to contact me.
Tuesday, August 31, 2010
Adding a printer
This is a re-post from the documentation site at http://sites.google.com/a/oregonsd.net/technology/documentation/add-a-printer added here for convenience.
The procedure for adding a printer is slightly different depending on if the computer is running WindowsXP or Windows 7. Both are shown below (scroll down for Windows 7).
The procedure for adding a printer is slightly different depending on if the computer is running WindowsXP or Windows 7. Both are shown below (scroll down for Windows 7).
Windows XP
- Click on the Start menu
- Select Settings, then Printers and Faxes
- Click Add a printer.
- In the "Add Printer Wizard," select A network printer, or a printer attached to another computer.
- Click Next
- Select Browse to a printer
- Click Next
- Click Find now. If you want to narrow the selection, you can optionally enter some information in the fields. In the example below, I have entered "HS" in the name, so that it will show only printers at the high school. You can do the same for the other buildings by entering BK, NK, PV, RC, MS, or DO.
- Click OK.
- A list of printers will appear. Scroll down and select the one you want, and double-click on its name.
- The printer drivers will be installed automatically. Be patient.
- Decide if you want this printer to be your default printer and select the appropriate choice.
- Click Next.
- Click Finish. Your printer will now appear as an option.
Windows 7
- Click on the Start menu and select Devices and Printers.
- Click Add a printer.
- Click Add a network, wireless or Bluetooth printer
- Click Next
- If you see the desired printer in the list, skip to step 8
- If you do not see the desired printer in the list, click The printer that I want isn't listed. This is a known bug.
- Click Next
- Select Find a printer in the directory, based on location or feature
- Click Next
- Click Find now. If you want to narrow the selection, you can optionally enter some information in the fields. In the example below, I have entered "HS" in the name, so that it will show only printers at the high school. You can do the same for the other buildings by entering BK, NK, PV, RC, MS, or DO.
- Click OK.
- A list of printers will appear. Scroll down and select the one you want, and double-click on its name.
- The printer drivers will be installed automatically. Be patient.
- A window will appear indicating a successful installation. Click Next.
- Decide if you want this printer to be your default printer and select the appropriate choice. Click Finish.
Monday, August 30, 2010
Security reminder- lock your computer while unattended
This is just a friendly reminder that when you leave your computer, even for just a second, you should lock your computer. Having the longest, most complex password in the world doesn't stop anybody if you leave your computer unlocked. It takes only seconds for somebody else to access data on your computer. In the past, we've had incidents including students changing grades, reading email, and even sending email from a teacher's account.
There are two easy ways to lock your computer. The quickest, easiest way is to press the Windows key and L on your keyboard. This will immediately lock your screen, requiring you to press Ctrl-Alt-Del and then enter your password to resume.
Alternatively, you could press Ctrl-Alt-Del and then click "Lock the Computer"
Please try to get in the habit of just pressing Windows-L as you leave your seat. This is a best practice that will greatly minimize the risk of unauthorized data access.
There are two easy ways to lock your computer. The quickest, easiest way is to press the Windows key and L on your keyboard. This will immediately lock your screen, requiring you to press Ctrl-Alt-Del and then enter your password to resume.
Alternatively, you could press Ctrl-Alt-Del and then click "Lock the Computer"
Please try to get in the habit of just pressing Windows-L as you leave your seat. This is a best practice that will greatly minimize the risk of unauthorized data access.
Friday, August 27, 2010
Where is my SmartBoard software?
Where is my SmartBoard software?
If it's not installed already, you can install it (and many other applications) by going to the Start menu, then the Zenworks Application Window, clicking on OregonSD and then the Multimedia group, and double-clicking on the SmartBoard Software icon. The software will download in the background, so you have to be patient. You can tell it's done when the program appears in the Start menu, or the SmartBoard tools icon appears in the task bar in the bottom right corner of the screen. See the attached screenshot.

If it's not installed already, you can install it (and many other applications) by going to the Start menu, then the Zenworks Application Window, clicking on OregonSD and then the Multimedia group, and double-clicking on the SmartBoard Software icon. The software will download in the background, so you have to be patient. You can tell it's done when the program appears in the Start menu, or the SmartBoard tools icon appears in the task bar in the bottom right corner of the screen. See the attached screenshot.
One Link to Rule Them All....
If you cannot find a work-related link you were looking for, it's probably at http://s.oregonsd.net/nav
This page is the replacement for the links that use to be on the OSD Start Page, before it was discontinued by Google. Now, you have both the Navigation page and a personal iGoogle page which you can customize to your heart's content.
This page is the replacement for the links that use to be on the OSD Start Page, before it was discontinued by Google. Now, you have both the Navigation page and a personal iGoogle page which you can customize to your heart's content.
Browser recommendations from Skyward and IT
Tech note from Skyward regarding supported Web Browser Versions:
The More You Know....
The latest versions of Firefox (PC), Safari (Mac) and Internet Explorer (PC) web browsers run well with Skyward’s Web applications. In performance tests, Firefox and Safari have actually performed slightly better than Internet Explorer.We (OSD IT) strongly recommend using Firefox for all general browsing due to its better speed, stability, and security versus IE. A few applications may still require the use of IE, so it will remain installed on Windows computers. IE 6 has been removed from all computers, and IE 7 is being replaced with IE 8 in an ongoing manner. IE 8 should be installed on all computers within the next six months. We do not officially support Safari or Google Chrome.
If your district uses Microsoft Internet Explorer (IE) version 7, we encourage you to upgrade to Internet Explorer version 8 because it runs Skyward's Web applications noticeably faster. The speed improvements in IE 8 are primarily due to improved processing of java script.
Although Google Chrome is not an officially tested web browser for Skyward, many customers have expressed interest in using this browser. Since Google Chrome follows basic web browser standards, it should work with the Skyward Web applications. If your district chooses to use Google Chrome, please report any issues to Skyward.
The More You Know....
Tuesday, August 24, 2010
New servers and drive letters- a quick overview
All the servers have been moved and renamed. Here's a cheat sheet including the shortcut drive letters on your computer.
H: is a shortcut to your home folder on a server called osd-home1\staff
S: is the place for sharing files internally with other staff. The share folders on the separate building servers have all been moved to a single server so that you can share more easily with staff from other buildings. These are now called "CommonShare" and are accessible at the S: drive. The building-specific folders are still intact, but that's just because we didn't want to mess with anybody's organization.
U: is where applications live. You don't really need to use this- it's just where the apps are stored.
V: is a big drive space for storing videos.
W: is a shortcut to a server called "osd-web1" which is (as you may have guessed) a web server. The public can get to this server at http://teachers.oregon.k12.wi.us Many teacher website are hosted here. Don't put anything here if you don't want it to be public.
Here is a screenshot of the local and network volumes as they appear on a Windows7 computer.
Thursday, August 12, 2010
Planned website outage Saturday, 8/14, 7-11 AM
SchoolWorld will be performing maintenance on the public website server on Saturday, August 14, 2010 from 8:00 AM - 12:00 PM ET. While there will not be a complete outage during the maintenance window, connectivity will be sporadic during the required server reboots. We appreciate your understanding.
PowerTeacher login blank
Staff Security Settings Screen: Teacher Login ID and Teacher Password intermittently blank
SUMMARY
PowerSchool administrators use the Staff Security Settings page to modify security settings for selected staff members. Intermittently the Teacher Login ID and Teacher Password are blank when the fields are populated with data. Refreshing the screen sometimes causes the Teacher Login ID and or Teacher Password to show. If the screen is submitted before being refreshed, the Teacher Login ID and Password may be overwritten and password will need to be reset.PREREQUISITE
- Teacher Login ID and Teacher Password fields were previously populated on the Staff Security Settings Screen.
REPRODUCTION
1. Log in to PowerSchool2. Start Page > Staff > Select A Staff Member
3. View Teacher Login ID and Teacher Password fields.
ACTUAL RESULT
Teacher Login ID And Teacher Password fields are empty.EXPECTED RESULT
Teacher Login ID and Teacher Password should display data.WORKAROUND
Refresh screen.Issue is being researched.
Wednesday, August 11, 2010
New website! (And how to get to the old one)
 Our new public website launched today! It has a great new look and more capabilities, including newsletter services, text alerts to parents, and easier editing of web pages.
Our new public website launched today! It has a great new look and more capabilities, including newsletter services, text alerts to parents, and easier editing of web pages.We are working on getting accounts created for all staff so you can log in and create your web pages on the new system. Staff who have pages on http://teachers.oregon.k12.wi.us (aka "the W: drive") can still access them at the old URL. Staff with pages on the old CMS server can access them at http://old.oregonsd.org
Once you have instructions for creating your new pages, you can copy and paste your content from your old site to the new one.
Tuesday, August 10, 2010
Change to Google Image Search mess individual image filtering
On July 20, 2010, Google introduced a new method to more efficiently return image results and provide an enhanced user experience. However, the results no longer include an individual link for each image. As a result, we are no longer able to provide the policy option to block Google image thumbnails by category.
We are still able to enforce the SafeSearch options with all of Google's search functions including image searching.
We know that Google is making every attempt to only return appropriate images with SafeSearch enabled. In the event an image is improperly returned as a SafeSearch result, you can report this image to Google here (requires Google login):
https://www.google.com/
When you issue a new removal request, you'll be prompted to provide a reason. Conveniently, one of the options is, "Inappropriate content appears in our SafeSearch filtered results."
If you would like to read more about Google's Image searching enhancements, you can find the details on its official blog: http://googleblog.blogspot.
If you have any questions or concerns, please contact me directly.
Sincerely,
Rob Chambers
robc@lightspeedsystems.com
Chief Technology Officer
Lightspeed Systems
661.716.7600
We are still able to enforce the SafeSearch options with all of Google's search functions including image searching.
We know that Google is making every attempt to only return appropriate images with SafeSearch enabled. In the event an image is improperly returned as a SafeSearch result, you can report this image to Google here (requires Google login):
https://www.google.com/
When you issue a new removal request, you'll be prompted to provide a reason. Conveniently, one of the options is, "Inappropriate content appears in our SafeSearch filtered results."
If you would like to read more about Google's Image searching enhancements, you can find the details on its official blog: http://googleblog.blogspot.
If you have any questions or concerns, please contact me directly.
Sincerely,
Rob Chambers
robc@lightspeedsystems.com
Chief Technology Officer
Lightspeed Systems
661.716.7600
Thursday, August 5, 2010
New public website goes live August 11
The Oregon School District's new public website will go live on August 11. To get a sneak preview of the new site, click here. The new site has many improvements, including optimized viewing on mobile devices, a newsletter system, and a professional look.
Instructions for logging in and editing pages will be provided to staff as soon as we have it available. We are still working on LDAP integration to allow staff to log in using their OSD password, instead of having to remember yet another password.
Instructions for logging in and editing pages will be provided to staff as soon as we have it available. We are still working on LDAP integration to allow staff to log in using their OSD password, instead of having to remember yet another password.
Friday, July 23, 2010
How to change your password
If you want to change your new password to something easier to remember, you can do online at https://db.oregon.k12.wi.us/saml/passchange.php (This is the direct link to the form, but you can also get to it when you are in Gmail -> Settings -> Accounts -> Google Account Settings -> Change Password. (Phew!))
Alternatively, if you are logged in to a computer at school, you can press Ctrl-Alt-Del and then click the "Change Password" button.
Remember, your new password must be fifteen characters or longer, and contain at least one of the following: capital letters, lowercase letters, numbers, and non-alphanumeric characters. If this sounds impossible, read the helpful guide for choosing complex passwords that are easy to remember but hard to guess.
Alternatively, if you are logged in to a computer at school, you can press Ctrl-Alt-Del and then click the "Change Password" button.
Remember, your new password must be fifteen characters or longer, and contain at least one of the following: capital letters, lowercase letters, numbers, and non-alphanumeric characters. If this sounds impossible, read the helpful guide for choosing complex passwords that are easy to remember but hard to guess.
Thursday, July 22, 2010
Server migration status update
The migration to new Active Directory servers is underway. You should now use your new password for most services that require your OSD password. This includes email, Google Apps, IT helpdesk, etc.
You will still need to use your old (Novell) password to access Skyward for the time being. We are working with Skyward to change their LDAP authentication configuration.
We are joining district computers to the Active Directory domain, but this is a time-consuming process, as we have to configure every computer manually. Until we are finished, you can determine which password to use to log in to a computer by looking at the login screen. If it has a Novell login window, use your old Novell login. If it does not have a Novell login window, press Ctrl-Alt-Del and enter your new password.
Monday, July 19, 2010
Rescheduled new password date: Thursday, July 22
The rescheduled date for moving to our new passwords is this Thursday, July 22. By this time, we should have all outstanding issues resolved and all files transferred from the old servers.
Due to the unpredictability of this process, I'm not going to specify a time of day during which the change will take place. In fact, it may affect different services and different users at different times. You should expect your old password to stop working sometime during the day on Thursday, at which time you should being using your new password.
As always, if you have questions, please contact the helpdesk.
Thanks for your patience.
Due to the unpredictability of this process, I'm not going to specify a time of day during which the change will take place. In fact, it may affect different services and different users at different times. You should expect your old password to stop working sometime during the day on Thursday, at which time you should being using your new password.
As always, if you have questions, please contact the helpdesk.
Thanks for your patience.
Friday, July 16, 2010
Keep using your Novell passwords, for now
The technical problem with delayed our switch to the new Active Directory passwords has been resolved... sorta. After many hours (thanks, Doug!) our technical support engineer friends were able to fix the problem with the service. Unfortunately, it required steps which mean we have to re-do much of the migration work we had already done prior to the glitch.
We have not determined a new cutover date or time, though it will likely be early next week, July 19 or 20. We will try to give you some advance notice, but I know many of you are really anxious to use your new passwords, so we may just make the configuration changes.
Your best course of action for now is to continue using your Novell passwords to access email until they no longer work, then try using your new Microsoft Active Directory password.
If you are trying to log on to a computer at school, take a look at the login screen. If it says "Novell" on it, use your old Novell password. If it doesn't say "Novell," use your new Microsoft Active Directory password.
We have not determined a new cutover date or time, though it will likely be early next week, July 19 or 20. We will try to give you some advance notice, but I know many of you are really anxious to use your new passwords, so we may just make the configuration changes.
Your best course of action for now is to continue using your Novell passwords to access email until they no longer work, then try using your new Microsoft Active Directory password.
If you are trying to log on to a computer at school, take a look at the login screen. If it says "Novell" on it, use your old Novell password. If it doesn't say "Novell," use your new Microsoft Active Directory password.
Wednesday, July 14, 2010
Technical difficulties may delay migration
This morning (yes, the day before our scheduled migration to Active Directory...[sigh]), a significant technical glitch reared its ugly head. Essentially, the service which deploys applications to the computers stopped working.
Doug worked on it for many hours, along with technical support from several companies. We do not have a solution yet. This may delay our scheduled migration. We have more things to try, but don't have an ETA.
What this means to you:
Basically, just continue using your Novell password until it no longer works. If it stops working, then try using the new AD password. This applies to logging into computers on campus as well as web-based services such as email and Google Apps.
We will post more updates here as necessary.
Doug worked on it for many hours, along with technical support from several companies. We do not have a solution yet. This may delay our scheduled migration. We have more things to try, but don't have an ETA.
What this means to you:
Basically, just continue using your Novell password until it no longer works. If it stops working, then try using the new AD password. This applies to logging into computers on campus as well as web-based services such as email and Google Apps.
We will post more updates here as necessary.
Thursday, July 1, 2010
Planned Internet outage July 14, 1:00 - 5:00 AM
Charter Communications will be performing maintenance that will affect the District's Internet connection on 7/14/2010, between 1:00 AM and 5:00 AM.
Description of Maintenance: Fitchburg, WI - Critical upgrade of chassis equipment to ensure optimum network performance and for future growth. This work involves powering down chassis, card removal, re-cabling, and then re-slotting cards and powering up new chassis.
Expected Down Time: 90 mins
Affected Sites or Services: Oregon SD
| Circuit ID | Circuit Description/Location | Impact |
| WOGWI09.26533 | 123 E. Grove St., Oregon, WI | 90 mins |
Charter Maintenance Ticket#: CRQ 23914
Wednesday, June 23, 2010
Servers to be frozen July 6-15(?)
On Friday, July 2, we will perform a final backup of all server data before migrating the data to the new servers. Starting July 6, data on the Novell servers will be migrated to the new Microsoft servers. Because we are moving more than 1 TB (yes, terabyte) of data while maintaining file permissions, this may take several days, and could last until the July 15 cutover to Active Directory. During this time, no changes can be made to data on the servers. You will be able to access data on the Novell servers, but will not be able to save any changes. We realize this will be an inconvenience for those of you working during the summer.
As a workaround, I highly recommend that you move any documents you need to work on during this time to Google Docs, which will allow you to access, modify, and share documents while the servers are "frozen." It is also a great way to access files from anywhere without any special software (Office, etc.)
If the migration goes more quickly than anticipated, we will turn on access to the Microsoft Servers ahead of the July 15 cutover date to give you access sooner.
Thanks for your patience during this major transition.
As a workaround, I highly recommend that you move any documents you need to work on during this time to Google Docs, which will allow you to access, modify, and share documents while the servers are "frozen." It is also a great way to access files from anywhere without any special software (Office, etc.)
If the migration goes more quickly than anticipated, we will turn on access to the Microsoft Servers ahead of the July 15 cutover date to give you access sooner.
Thanks for your patience during this major transition.
Changes to personalized Start Page
Google has informed us that beginning July 1, they will no longer support the personalized start page that we have been using. The page will be replaced with an iGoogle page, which is completely customizable by each user. This means that we can no longer publish the district's links that you currently see on the left column of your personalized page. To fix this, we are creating a second page which will contain the district links which you can customize. We will roll this out soon. Until then, you can add the links you use frequently to your own customized iGoogle page. Sorry for any confusion this may cause.
Wednesday, June 2, 2010
Summer computer checkout request form
If you want to check out a notebook computer over the summer, you need to check out one from the tech office, not your school. All computers must be migrated from Novell to Microsoft Active Directory this summer, so they may not be checked out from schools as in past years. We have a limited number of computers we can check out from the DSO for summer use.
Submit a request using the form at
http://spreadsheets.google.
You can also access the form by going to the IT Document site at http://sites.google.com/a/
Bear in mind that we have a limited number of computers available, so you should check one out for the shortest amount of time necessary so that we have enough for everyone.
http://spreadsheets.google.
You can also access the form by going to the IT Document site at http://sites.google.com/a/
Bear in mind that we have a limited number of computers available, so you should check one out for the shortest amount of time necessary so that we have enough for everyone.
Friday, May 28, 2010
Skyward phishing scam
We just received this from Skyward. Please be aware.
It has come to our attention through one of our customers that there is a phishing scam that appears to be coming from Skyward. Skyward would not send you a link and ask that you log into it. The email address this came from is skywardhelp@cyberservices.com [mailto:skywardhelp@cyberservices.com]. This is not a valid email address for Skyward. Please instruct your users to ignore any type of request like this.
We appreciate your prompt attention to this matter. If you have any questions, please contact Skyward Customer Service.
Thank You - Skyward Support Staff
SN #1474
Do you have your new password ready?
Do you have your fifteen character password ready?
This is a reminder that starting July 15, all staff must have a long password. New passwords must be at least fifteen characters long and contain at least one number and symbol.
The good news? Your password will not expire, so you won't ever have to change it unless it gets cracked.
If you are wondering why, or need help creating a password that long that you can also remember, please read "How to choose a good password" on our documentation site.
On July 15, we will switch our servers from Novell to Microsoft. This means your current Novell password will no longer work, and you will have to start using a new one. Because we cannot see or export your current passwords, we will assign you a new one that you must start using on July 15.
Before the end of school, you will receive a piece of paper which will contain your new password. On July 15, you will need to start using this new password. You may want to change it to something you can remember more easily, but you must use the password issued to you at least once to log in and change your password.
If you have questions, please feel free to contact me or read the detailed explanation at http://sites.google.com/a/oregonsd.net/technology-integration-tool/Home/passwords (staff login required).
This is a reminder that starting July 15, all staff must have a long password. New passwords must be at least fifteen characters long and contain at least one number and symbol.
The good news? Your password will not expire, so you won't ever have to change it unless it gets cracked.
If you are wondering why, or need help creating a password that long that you can also remember, please read "How to choose a good password" on our documentation site.
On July 15, we will switch our servers from Novell to Microsoft. This means your current Novell password will no longer work, and you will have to start using a new one. Because we cannot see or export your current passwords, we will assign you a new one that you must start using on July 15.
Before the end of school, you will receive a piece of paper which will contain your new password. On July 15, you will need to start using this new password. You may want to change it to something you can remember more easily, but you must use the password issued to you at least once to log in and change your password.
If you have questions, please feel free to contact me or read the detailed explanation at http://sites.google.com/a/oregonsd.net/technology-integration-tool/Home/passwords (staff login required).
Thursday, April 29, 2010
Bogus email
A number of people have received the following message:
Our content filter identifies the linked site as a virus site. If you clicked on the link, please submit a helpdesk ticket so we can check your computer for virus infections.
------Original Message------This is false message and is not from us. You can tell this is a fake easily because the originating email address is not from the district, and the URL it asks you to click is not from the district.
From: Webmail Administrator
To: undisclosed-recipients:;
Subject: Webmail Upgrade
Sent: Apr 29, 2010 2:50 AM
Dear Email User,
We are upgrading our Email system to enable us reduce the occurrence of spam .
You are to clink on the Link below to Upgrade your Email.
[link has been removed so we don't infect anybody]
Signed,
Webmaster Administration
Our content filter identifies the linked site as a virus site. If you clicked on the link, please submit a helpdesk ticket so we can check your computer for virus infections.
Wednesday, April 28, 2010
Unplanned Internet outage now resolved
A brief Internet outage has been resolved. Here is the notification from WiscNet.
The routing process on the ISP router in Madison was restarted to
restore connectivity. Network Engineers have opened a case with
the vendor to investigate the cause of the outage.
Network: WiscNetMaria Accuardi @ 2010-04-28 10:35:56
Type: Unplanned Outage
Location: WiscNet
Ticket Number: 107176
Party:
Start Time: 4/28/2010 9:40 CDT
End Time: Unknown
Description: Widespread Outage
Engineers:
Reporters:
Affected:
WiscNet Members
Notices:
Maria Accuardi @ 2010-04-28 09:59:31
There is a widespread outage for WiscNet members at this time.
Network Engineers are currently working to resolve the issue.
Maria Accuardi @ 4/28/2010 9:59 CDT
The routing process on the ISP router in Madison was restarted to
restore connectivity. Network Engineers have opened a case with
the vendor to investigate the cause of the outage.
Wednesday, April 21, 2010
Proposed new password policies for next year
New password policies for next year
I am proposing two big changes to the district's password policy. The two big changes are: 1) Passwords will never automatically expire; and 2) Passwords will have to be fifteen characters long and have some complexity. These go hand-in-hand. If the passwords are long and complex, they probably won't be cracked, so they won't ever need to be changed.
Why will they never expire?
Research on IT best practices shows that the more frequently passwords are changed, the simpler they become. We also know that changing a password regularly doesn't necessarily stop bad things from happening- it simply blocks out an intruder who happens to get your password. Also, we know it's annoying when passwords expire.
Why will they have to be fifteen characters long?
Again, IT best practices show that long, complex passwords are more secure. There are many reasons for this, but there are two I'm focusing on.
First, there is a very easy password cracking tool that students use (yes, even Oregon students have used this) which can crack any Windows password with a length of fourteen characters or less. Adding the fifteenth character might not seem like much, but the exponential increase in complexity, combined with the way that Windows hashes passwords makes this a huge difference. The second reason for complex passwords is that if a student happens to see or hear a password, it should be something that's difficult to remember. For example if you write down your password (in your wallet or some other place where people won't see it) and a student catches a glimpse, they could remember "BrianJoeErica1990" more easily than "mfdwmfswam3m0ri@lu"
How can we remember all that gibberish?!?
The secret is that it's not really gibberish. The password above, "mfdwmfswaM3m0ri@lU" only looks like gibberish. In fact, it's based on a phrase that has significant personal meaning: "My first date with my future spouse was at Memorial Union." (I just made this up, it's not true, but if it were, it would be memorable. Choose your own phrase.)
See how I got the password? I took the first letter of each word, then the entire word "Memorial" but substituted a "3" for the "e", a zero for the "o", and an "@" for the "a". The resulting password has lots of complexity- it includes capital and lowercase letters, numbers, and symbols. And after a while, your fingers will just get used to typing it. Remember- you won't have to change it every month.
Related resources:
I am proposing two big changes to the district's password policy. The two big changes are: 1) Passwords will never automatically expire; and 2) Passwords will have to be fifteen characters long and have some complexity. These go hand-in-hand. If the passwords are long and complex, they probably won't be cracked, so they won't ever need to be changed.
Why will they never expire?
Research on IT best practices shows that the more frequently passwords are changed, the simpler they become. We also know that changing a password regularly doesn't necessarily stop bad things from happening- it simply blocks out an intruder who happens to get your password. Also, we know it's annoying when passwords expire.
Why will they have to be fifteen characters long?
Again, IT best practices show that long, complex passwords are more secure. There are many reasons for this, but there are two I'm focusing on.
First, there is a very easy password cracking tool that students use (yes, even Oregon students have used this) which can crack any Windows password with a length of fourteen characters or less. Adding the fifteenth character might not seem like much, but the exponential increase in complexity, combined with the way that Windows hashes passwords makes this a huge difference. The second reason for complex passwords is that if a student happens to see or hear a password, it should be something that's difficult to remember. For example if you write down your password (in your wallet or some other place where people won't see it) and a student catches a glimpse, they could remember "BrianJoeErica1990" more easily than "mfdwmfswam3m0ri@lu"
How can we remember all that gibberish?!?
The secret is that it's not really gibberish. The password above, "mfdwmfswaM3m0ri@lU" only looks like gibberish. In fact, it's based on a phrase that has significant personal meaning: "My first date with my future spouse was at Memorial Union." (I just made this up, it's not true, but if it were, it would be memorable. Choose your own phrase.)
See how I got the password? I took the first letter of each word, then the entire word "Memorial" but substituted a "3" for the "e", a zero for the "o", and an "@" for the "a". The resulting password has lots of complexity- it includes capital and lowercase letters, numbers, and symbols. And after a while, your fingers will just get used to typing it. Remember- you won't have to change it every month.
Related resources:
Thursday, April 15, 2010
Tuesday, April 13, 2010
ROME server reboot
The server unmounted its volumes at about 1:15pm today, April 13th 2010. I rebooted it, and it was back up and running by 1:25pm
Monday, April 12, 2010
ROME server reboot
9:45 AM on Monday April 12 --
The Rome Corners server encountered a driver error and had to be rebooted. The server was back online by approximately 10:00 AM.
The Rome Corners server encountered a driver error and had to be rebooted. The server was back online by approximately 10:00 AM.
Thursday, April 8, 2010
Elementary server problems
The server for all three elementary schools has been behaving badly. It experienced numerous freezes and reboots which resulted in users not seeing files, taking 10-20 minutes to log in, and causing programs to crash.
A Novell consultant has been working on the problem with us since this morning. We haven't found a definite problem, but there are some abnormalities with the server. We are currently copying the server to different hard drives in hopes of resolving the problem. Unfortunately, it's going very slowly (which in itself is a bad sign, and means it could very well be a problem with the drives). It took one hour for 25 GB of data to transfer, and the whole data set is over 400 GB in size, which means the transfer will take 16 hours.
We will try to get the server working again by the morning. We know you have lots of important things stored on there, and we are trying our best to give you access again without losing anything. Thanks for your patience.
Further updates as events warrant.
A Novell consultant has been working on the problem with us since this morning. We haven't found a definite problem, but there are some abnormalities with the server. We are currently copying the server to different hard drives in hopes of resolving the problem. Unfortunately, it's going very slowly (which in itself is a bad sign, and means it could very well be a problem with the drives). It took one hour for 25 GB of data to transfer, and the whole data set is over 400 GB in size, which means the transfer will take 16 hours.
We will try to get the server working again by the morning. We know you have lots of important things stored on there, and we are trying our best to give you access again without losing anything. Thanks for your patience.
Further updates as events warrant.
Internet down for whole district
UPDATE
This is the official ticket for the 42 minute Internet access outage this morning.
Network: WiscNet
Type: Unplanned Outage
Location: Madison
Ticket Number: 100354
Party: Charter
Start Time: 4/8/2010 8:19 CDT
End Time: 4/8/2010 9:01 CDT
Description: Multiple Charter Site Outage
Engineers:
Reporters:
Affected:
r-beloitsd
r-berlinsd
r-bigfooths
r-columbussd
r-delavandariensd
r-dodgevillesd
r-edgertonsd
r-fonddulacsd
r-linnbloomfieldsd
r-madisontc
r-mcfarlandsd
r-newglarussd
r-newholsteinsd
r-oregonsd
r-reedsburgsd
r-richfieldsd
r-rosendalesd
r-slingersd
r-walworthsd
Notices:
Maria Accuardi @ 2010-04-08 09:16:12
Multiple Charter sites failed at 0819. The WiscNet and Charter
Engineers are investigating the cause of the outage. Connectivity
was restored to all sites at 0901.
Maria Accuardi @ 4/8/2010 9:16 CDT
This is the official ticket for the 42 minute Internet access outage this morning.
Network: WiscNet
Type: Unplanned Outage
Location: Madison
Ticket Number: 100354
Party: Charter
Start Time: 4/8/2010 8:19 CDT
End Time: 4/8/2010 9:01 CDT
Description: Multiple Charter Site Outage
Engineers:
Reporters:
Affected:
r-beloitsd
r-berlinsd
r-bigfooths
r-columbussd
r-delavandariensd
r-dodgevillesd
r-edgertonsd
r-fonddulacsd
r-linnbloomfieldsd
r-madisontc
r-mcfarlandsd
r-newglarussd
r-newholsteinsd
r-oregonsd
r-reedsburgsd
r-richfieldsd
r-rosendalesd
r-slingersd
r-walworthsd
Notices:
Maria Accuardi @ 2010-04-08 09:16:12
Multiple Charter sites failed at 0819. The WiscNet and Charter
Engineers are investigating the cause of the outage. Connectivity
was restored to all sites at 0901.
Maria Accuardi @ 4/8/2010 9:16 CDT
Wednesday, March 31, 2010
Spring Break Server Outages: Updates
All Novell building servers will be shut down this afternoon, beginning at 3:45 for approximately 1 hour. Check back here for further updates after 5:00 p.m.
FINAL UPDATE: MIDDLE is back online!!!!!
FINAL UPDATE: MIDDLE is back online!!!!!
Tuesday, March 30, 2010
Spring Break Server Outages
Some maintenance work for all Novell servers tonight through tomorrow morning. (for anyone in the buildings..)
MIDDLE will be shut down today (March 30) at approximately 3:00 p.m. and expected to return to service tomorrow morning.
All other building servers (DSO, PANTHER, ROME, PVE) will be shut down tomorrow morning at approximately 6:00 a.m. for disc upgrades. All servers are expected to be returned to service by 7:00 a.m. on March 31st.
Tuesday, March 23, 2010
Skyward Self-Service link visibility workaround
The link to Skyward Self-Service on the staff start page has been moved to the top of the Online Tools section so that it will be consistently visible regardless of the web browser you use. The widgets on the start page sometimes don't resize correctly, resulting in the bottom few items being cut off.
Unfortunately, it seems to be a sporadic problem, so we haven't found a way to fix it for everyone yet. We do know that Firefox is the best browser to use because it renders the HTML most consistently. If you are using Chrome or Internet Explorer, your chances of encountering the problem are greatly increased.
Obviously, we will fix it as soon as we find the solution, but until then, the combination of moving the link to the top of the list, and using Firefox, should fix it for most everyone. Just for your reference, the link is https://skywardea-win.iscorp.com/cgi-bin10/cgiip.exe/WService=wsermaoregonwi/seplog01.w
Unfortunately, it seems to be a sporadic problem, so we haven't found a way to fix it for everyone yet. We do know that Firefox is the best browser to use because it renders the HTML most consistently. If you are using Chrome or Internet Explorer, your chances of encountering the problem are greatly increased.
Obviously, we will fix it as soon as we find the solution, but until then, the combination of moving the link to the top of the list, and using Firefox, should fix it for most everyone. Just for your reference, the link is https://skywardea-win.iscorp.com/cgi-bin10/cgiip.exe/WService=wsermaoregonwi/seplog01.w
Thursday, February 11, 2010
OHS wireless interruption
What: Network maintenance causing an interruption in wireless connectivity.
When: Feb 11 from 4:00PM until 4:30PM
Who: Most people who use wireless at OHS after school hours will be affected.
Where: The entire northern half of the OHS building. (the north end is where the IMC is)
Why: We will replacing some old network equipment at OHS. This is will be the first of two maintenance windows required to complete the cut-over.
How: This question word really isn't needed, but I thought I'd stick it on the end to complete the set.
When: Feb 11 from 4:00PM until 4:30PM
Who: Most people who use wireless at OHS after school hours will be affected.
Where: The entire northern half of the OHS building. (the north end is where the IMC is)
Why: We will replacing some old network equipment at OHS. This is will be the first of two maintenance windows required to complete the cut-over.
How: This question word really isn't needed, but I thought I'd stick it on the end to complete the set.
Monday, February 8, 2010
IT Initiatives 2010
Here is a brief presentation outlining the major initiatives of the next eight months. Remember, change is good!
Wednesday, February 3, 2010
Annenberg videos and lessons available free
Did you know we have a partnership with the Annenberg / CPB Foundation and UW Madison DoIT Streaming Media Services to make Annenberg's Video On Demand (VOD) courses available to you direct from the WiscNet network? Annenberg makes a large number of high quality VOD teacher resources available to the public from their web site at http://www.learner.org/ The VOD courses take the form of Microsoft Windows Media Player streaming videos.
Annenberg has worked with a number of local, regional and state networks to create local content mirrors. The way their setup works is that when you select a VOD course to view from the Annenberg site (http://www.learner.org/), their site detects that you are on the WiscNet network and redirects your request to the WiscNet content mirror. You then receive the video stream you selected from WiscNet's content mirror.
The benefit to you of WiscNet hosting an Annenberg content is that when you view an Annenberg VOD course your stream is coming to you directly from the WiscNet backbone, NOT from the Internet! This only applies when you are viewing them from school. You can still access all the content from off campus, but the performance may not be as good, depending on your Internet connection speeds.
Annenberg has worked with a number of local, regional and state networks to create local content mirrors. The way their setup works is that when you select a VOD course to view from the Annenberg site (http://www.learner.org/), their site detects that you are on the WiscNet network and redirects your request to the WiscNet content mirror. You then receive the video stream you selected from WiscNet's content mirror.
The benefit to you of WiscNet hosting an Annenberg content is that when you view an Annenberg VOD course your stream is coming to you directly from the WiscNet backbone, NOT from the Internet! This only applies when you are viewing them from school. You can still access all the content from off campus, but the performance may not be as good, depending on your Internet connection speeds.
Tuesday, February 2, 2010
Older browsers won't be supported in Google Apps
Google Apps sent out the following notice regarding the end of support for older browsers. I'm passing along this notice in case anyone is using an older browser at home. All district computers have been upgraded to supported browsers.
In order to continue to improve our products and deliver more sophisticated features and performance, we are harnessing some of the latest improvements in web browser technology. This includes faster JavaScript processing and new standards like HTML5. As a result, over the course of 2010, we will be phasing out support for Microsoft Internet Explorer 6.0 as well as other older browsers that are not supported by their own manufacturers.So, if you are still running IE 6, Firefox 2, or some ancient version of Netscape, it's time to upgrade.
We plan to begin phasing out support of these older browsers on the Google Docs suite and the Google Sites editor on March 1, 2010. After that point, certain functionality within these applications may have higher latency and may not work correctly in these older browsers. Later in 2010, we will start to phase out support for these browsers for Google Mail and Google Calendar.
Google Apps will continue to support Internet Explorer 7.0 and above, Firefox 3.0 and above, Google Chrome 4.0 and above, and Safari 3.0 and above.
Starting this week, users on these older browsers will see a message in Google Docs and the Google Sites editor explaining this change and asking them to upgrade their browser. We will also alert you again closer to March 1 to remind you of this change.
In 2009, the Google Apps team delivered more than 100 improvements to enhance your product experience. We are aiming to beat that in 2010 and continue to deliver the best and most innovative collaboration products for businesses.
Thank you for your continued support!
Sincerely,
The Google Apps team
Saturday, January 23, 2010
DSO Server down for maintenance
The DSO server was shutdown this morning at 08:31. The work shuold continue until approximately 7:00 p.m.
For those that are curious - prior to today, this server had been up continuously for 176 days, 13 hours and 24 minutes.
For those that are curious - prior to today, this server had been up continuously for 176 days, 13 hours and 24 minutes.
Friday, January 22, 2010
Critical Internet Explorer security vulnerability patch
If you remember hearing about Google and other companies getting hacked by China, it was due to a security hole in Microsoft Internet Explorer. Microsoft is releasing an emergency security patch to solve this issue.
Please patch your home computers.
Please patch your home computers.
| What is the purpose of this alert? |
This alert is to provide you with an overview of the new security bulletin being released (out-of-band) on January 21, 2010.
New Security Bulletin
Microsoft is releasing one new security bulletin (out-of-band) for newly discovered vulnerabilities:
| Bulletin ID | Bulletin Title | Maximum Severity Rating | Vulnerability Impact | Restart Requirement | Affected Software |
| MS10-002 | Cumulative Security Update for Internet Explorer (978207) | Critical | Remote Code Execution | Requires a restart | All supported versions of Internet Explorer on Windows 2000, Windows XP, Windows Server 2003, Windows Vista, Windows Server 2008*, Windows 7, and Windows Server 2008 R2*. |
| * Where indicated in the Affected Software table on the bulletin Web page, the vulnerabilities addressed by this update do not affect supported editions of Windows Server 2008 or Windows Server 2008 R2, when installed using the Server Core installation option. Please see the bulletin Web page at the link in the left column for more details. |
Public Bulletin Webcast
Microsoft will host a webcast to address customer questions on this bulletin:
Title: Information About Microsoft's January 2010 Out-of-Band Security Bulletin Release
Date: Thursday, January 21, 2010, at 1:00 P.M. Pacific Time (U.S. & Canada).
Public Resources related to this alert
- Security Bulletin MS10-002 – Cumulative Security Update for Internet Explorer (978207):
http://www.microsoft.com/technet/security/bulletin/ MS10-002.mspx
- Microsoft Security Response Center (MSRC) Blog: http://blogs.technet.com/msrc/
- Microsoft Security Research & Defense (SRD) Blog: http://blogs.technet.com/srd/
- Microsoft Malware Protection Center (MMPC) Blog: http://blogs.technet.com/mmpc/
- Microsoft Security Development Lifecycle (SDL) Blog: http://blogs.msdn.com/sdl/
New Security Bulletin Technical Details
In the following tables of affected and non-affected software, software editions that are not listed are past their support lifecycle. To determine the support lifecycle for your product and edition, visit the Microsoft Support Lifecycle Web site at http://support.microsoft.com/
| Bulletin Identifier | Microsoft Security Bulletin MS10-002 | |
| Bulletin Title | Cumulative Security Update for Internet Explorer (978207) | |
| Executive Summary | This security update resolves seven privately reported vulnerabilities and one publicly disclosed vulnerability in Internet Explorer. The more severe vulnerabilities could allow remote code execution if a user views a specially crafted Web page using Internet Explorer. The security update addresses these vulnerabilities by modifying the way that Internet Explorer handles objects in memory, validates input parameters, and filters HTML attributes. This security update also addresses the vulnerability first described in Microsoft Security Advisory 979352. | |
| Affected Software | All supported versions of Internet Explorer on Windows 2000, Windows XP, Windows Server 2003, Windows Vista, Windows Server 2008*, Windows 7, and Windows Server 2008 R2*. * Where indicated in the Affected Software table on the bulletin Web page, the vulnerabilities addressed by this update do not affect supported editions of Windows Server 2008 or Windows Server 2008 R2, when installed using the Server Core installation option. Please see the bulletin Web page at the link below for more details. | |
| CVE, Exploitability Index Rating |
Note: Please see the Exploitability Index table of the bulletin summary page for more details: http://www.microsoft.com/ | |
| Attack Vectors |
| |
| Mitigating Factors |
| |
| Restart Requirement | The update will require a restart. | |
| Bulletins Replaced by This Update | MS09-072 |
| Publicly Disclosed? Exploited? | CVE-2010-0249 has been publicly disclosed prior to release. CVE-2010-0249 has been exploited in the wild at release. |
| Full Details | http://www.microsoft.com/ |
Regarding Information Consistency
We strive to provide you with accurate information in static (this mail) and dynamic (Web-based) content. Microsoft’s security content posted to the Web is occasionally updated to reflect late-breaking information. If this results in an inconsistency between the information here and the information in Microsoft’s Web-based security content, the information in Microsoft’s Web-based security content is authoritative.
If you have any questions regarding this alert please contact your Technical Account Manager or Application Development Consultant.
Thank you,
Microsoft CSS Security Team
Heidi Felker
Education Account Manager - US Public Sector
Microsoft Corporation
One Microsoft Way
Redmond, Washington 98052
Toll Free (800) 426 - 9400 x 11310
Direct: (425) 704-6563
Email: heidife@microsoft.com
Security alert- new types of attacks
[This is from another university that granted permission to share as long as
I didn't say where it came from.]
Folks,
Over the past week or so, we've seen a marked increase in malicious
advertisements targeting (and exploiting) multiple vulnerabilities -
including ones in Java Runtime Environment (JRE) and Java Development
Kit (JDK) - to silently download and install malware. We have learned
of three "advertising agencies" that appear to be operated by the same
group, that are completely bogus, and they have gotten their ads
pushed out via the largest advertisers in the business. We've seen
popular local and world news sites, popular greeting card sites,
screen saver sites, and more "displaying" these ads. The number and
size of legitimate advertising agencies that wind up referring users
to these malicious advertisements basically means that every Web site
that outsources advertising should be considered a potential infection
vector.
While malicious ads targeting Adobe Flash Player and Adobe
Reader/Acrobat have been going on for well over a year, this is the
first time I can remember seeing numerous computers becoming infected
daily due to a JRE/JDK exploit.
I was able to successfully recreate an infection simply by visiting a
very popular (legitimate) greeting card site this morning. I did not
get redirected to any visible fake AV site, nor did I have to interact
with anything to become infected. There no visible symptoms of an
infection for several minutes, before the fake AV software finally
reared its ugly head. And it wasn't just a Web page that popped up -
it had been silently installed.
This particular variant prevented many Windows applications from
running, including (but not limited to) Paint, cmd.exe, Control Panel,
and more. This fake AV installs itself in a manner that allows
infection of limited user accounts - admin privileges are not needed.
And the kicker... the sample that I sent to virustotal.com was
detected by one out of 41 AV vendors (Symantec wasn't the one).
We have seen signs that not all hosts infected via these advertising
campaigns get the fake Antivirus software package - however, we are
not sure what is downloaded and installed on those hosts. Assuming it
is malware, it evades all of our existing detection methods.
We've seen Java versions 1.6.x up to 1.6.0_15 become compromised, as
well as several 1.5.x versions. We've seen a host running 1.6.0_17
that did not become compromised, leading us to believe that the most
recent Java security release (1.6.0_17) fixes the vulnerability that
this group is exploiting.
Note that a (presumably) different group of miscreants has been using
bogus advertisements that redirect the browser window to fake AV Web
sites. That site will then try (hard) to convince the user to download
and install their product. That activity is not typically indicative
of an infection - and is an entirely different user experience than
the one I mentioned above. And while we saw a rash of this a few weeks
ago, it seems that almost all of the fake AV we've seen over the past
week was installed silently via drive-by exploits.
I cannot stress enough the magnitude of this situation. The popularity
of the Web sites that we've seen host these "advertisements" is
incredibly high - several of them surely get several thousand hits a
day. Thankfully not everyone who goes to these sites gets the evil ads,
but it is a game of Russian roulette that simply isn't worth playing.
We will be tracking this group as best as we can, and taking
network-wide mitigation steps where appropriate (and possible). But
this group changes their M.O. frequently, and I feel they clearly have
gotten to the point where they aren't going away without handcuffs or
pointy lead.
On a similar note, over the course of the last year or so, several AV
vendors have noticed an uptick in malware that encrypts all of certain
types of data files on the computer, and demands a ransom for the
decryption key. Many folks (including myself) think that it is just a
matter of time before that becomes a much more common payload for
these large drive-by malicious advertising campaigns.
And finally, a personal plea. Please - if you or someone you know
comes across this... don't *ever* decide to purchase the fake AV -
even though it might seem to be the easiest way out. Not only is this
financing their operation, this is giving your credit card info to
some serious (and rather bold) criminals.
I didn't say where it came from.]
Folks,
Over the past week or so, we've seen a marked increase in malicious
advertisements targeting (and exploiting) multiple vulnerabilities -
including ones in Java Runtime Environment (JRE) and Java Development
Kit (JDK) - to silently download and install malware. We have learned
of three "advertising agencies" that appear to be operated by the same
group, that are completely bogus, and they have gotten their ads
pushed out via the largest advertisers in the business. We've seen
popular local and world news sites, popular greeting card sites,
screen saver sites, and more "displaying" these ads. The number and
size of legitimate advertising agencies that wind up referring users
to these malicious advertisements basically means that every Web site
that outsources advertising should be considered a potential infection
vector.
While malicious ads targeting Adobe Flash Player and Adobe
Reader/Acrobat have been going on for well over a year, this is the
first time I can remember seeing numerous computers becoming infected
daily due to a JRE/JDK exploit.
I was able to successfully recreate an infection simply by visiting a
very popular (legitimate) greeting card site this morning. I did not
get redirected to any visible fake AV site, nor did I have to interact
with anything to become infected. There no visible symptoms of an
infection for several minutes, before the fake AV software finally
reared its ugly head. And it wasn't just a Web page that popped up -
it had been silently installed.
This particular variant prevented many Windows applications from
running, including (but not limited to) Paint, cmd.exe, Control Panel,
and more. This fake AV installs itself in a manner that allows
infection of limited user accounts - admin privileges are not needed.
And the kicker... the sample that I sent to virustotal.com was
detected by one out of 41 AV vendors (Symantec wasn't the one).
We have seen signs that not all hosts infected via these advertising
campaigns get the fake Antivirus software package - however, we are
not sure what is downloaded and installed on those hosts. Assuming it
is malware, it evades all of our existing detection methods.
We've seen Java versions 1.6.x up to 1.6.0_15 become compromised, as
well as several 1.5.x versions. We've seen a host running 1.6.0_17
that did not become compromised, leading us to believe that the most
recent Java security release (1.6.0_17) fixes the vulnerability that
this group is exploiting.
Note that a (presumably) different group of miscreants has been using
bogus advertisements that redirect the browser window to fake AV Web
sites. That site will then try (hard) to convince the user to download
and install their product. That activity is not typically indicative
of an infection - and is an entirely different user experience than
the one I mentioned above. And while we saw a rash of this a few weeks
ago, it seems that almost all of the fake AV we've seen over the past
week was installed silently via drive-by exploits.
I cannot stress enough the magnitude of this situation. The popularity
of the Web sites that we've seen host these "advertisements" is
incredibly high - several of them surely get several thousand hits a
day. Thankfully not everyone who goes to these sites gets the evil ads,
but it is a game of Russian roulette that simply isn't worth playing.
We will be tracking this group as best as we can, and taking
network-wide mitigation steps where appropriate (and possible). But
this group changes their M.O. frequently, and I feel they clearly have
gotten to the point where they aren't going away without handcuffs or
pointy lead.
On a similar note, over the course of the last year or so, several AV
vendors have noticed an uptick in malware that encrypts all of certain
types of data files on the computer, and demands a ransom for the
decryption key. Many folks (including myself) think that it is just a
matter of time before that becomes a much more common payload for
these large drive-by malicious advertising campaigns.
And finally, a personal plea. Please - if you or someone you know
comes across this... don't *ever* decide to purchase the fake AV -
even though it might seem to be the easiest way out. Not only is this
financing their operation, this is giving your credit card info to
some serious (and rather bold) criminals.
Monday, January 18, 2010
wifi status update
You may have started to see some weird-looking electronic devices popping up on the ceilings your schools. No, you need not start wearing a tin-foil hat; we're not trying to read your thoughts. Each of these is a wireless access point (AP) that you can connect to with a laptop, iTouch, or your bathroom scale if you just happen to own one of these.
For the almost a year now we at the tech office have been planning, installing and testing the new wireless network at Oregon High School and Oregon Middle School. We are proud to say that we are now running at full speed in both locations.
What this means for you:
In your classroom at OMS or OHS you will now have network access for the many wireless devices that are either housed in your classroom, or that you may bring in from home. There are two wireless network names (SSID) being broadcast. The first one is called "osd" and the second is called "public". Any device that you bring from home may connect to "public" without even needing a password. All devices that are maintained by OSD, and have anti-virus software installed are set up to connect to "osd".
The difference between osd and public is simply this:
When you connect to "public" you will have the same access as if you were sitting at home(although filtered to meet CIPA compliance). You may connect to sites on the internet and any publicly accessible OSD sites (PowerTeacher, PowerSchool, Email, etc...). When connected to "osd" on a device owned by The District, you will have access to log into Novell and get to your files on the H, V, W,(...etc) drives.
eeePCs:
Most of these do not have antivirus software available, and are not regularly patched by OSD so the majority these will also connect to "public".
What about my building / classroom??
We have wireless coverage in all classrooms in OHS, OMS and RCI. So far we have limited coverage at the elementary buildings, but we're are working hard to get wireless where it's needed as soon as possible. If you're you're having trouble getting connected in your classroom at OHS, OMS or RCI please let us know and we'll get it figured out for you.
Thanks and enjoy your WPA2 AES encrypted IEEE802.11N-2009 2.4 / 5GHz connections!
Your friendly neighborhood IT department.
A final thought to leave you with:
“The wireless telegraph is not difficult to understand. The ordinary telegraph is like a very long cat. You pull the tail in New York, and it meows in Los Angeles. The wireless is the same, only without the cat.”
-Albert Einstein
For the almost a year now we at the tech office have been planning, installing and testing the new wireless network at Oregon High School and Oregon Middle School. We are proud to say that we are now running at full speed in both locations.
What this means for you:
In your classroom at OMS or OHS you will now have network access for the many wireless devices that are either housed in your classroom, or that you may bring in from home. There are two wireless network names (SSID) being broadcast. The first one is called "osd" and the second is called "public". Any device that you bring from home may connect to "public" without even needing a password. All devices that are maintained by OSD, and have anti-virus software installed are set up to connect to "osd".
The difference between osd and public is simply this:
When you connect to "public" you will have the same access as if you were sitting at home(although filtered to meet CIPA compliance). You may connect to sites on the internet and any publicly accessible OSD sites (PowerTeacher, PowerSchool, Email, etc...). When connected to "osd" on a device owned by The District, you will have access to log into Novell and get to your files on the H, V, W,(...etc) drives.
eeePCs:
Most of these do not have antivirus software available, and are not regularly patched by OSD so the majority these will also connect to "public".
What about my building / classroom??
We have wireless coverage in all classrooms in OHS, OMS and RCI. So far we have limited coverage at the elementary buildings, but we're are working hard to get wireless where it's needed as soon as possible. If you're you're having trouble getting connected in your classroom at OHS, OMS or RCI please let us know and we'll get it figured out for you.
Thanks and enjoy your WPA2 AES encrypted IEEE802.11N-2009 2.4 / 5GHz connections!
Your friendly neighborhood IT department.
A final thought to leave you with:
“The wireless telegraph is not difficult to understand. The ordinary telegraph is like a very long cat. You pull the tail in New York, and it meows in Los Angeles. The wireless is the same, only without the cat.”
-Albert Einstein
Sunday, January 17, 2010
Server Maintenance
PVE is returned to service at 8:35 a.m. Sunday
PANTHER will now be shutdown to move from temporary location to the SAN
PANTHER will now be shutdown to move from temporary location to the SAN
Tuesday, January 12, 2010
Slow logins at OHS- status, explanation
The helpdesk has fielded a number of complaints about slow logins from OHS. After researching the issue, our current theory is that the FreeNAS array currently holding the PANTHER server is slower than the regular SAN or drive arrays in the servers. PANTHER is being temporarily hosted on FreeNAS until it can be moved to the SAN. However, we can't fully migrate it until other arrays have been moved, which we were doing last weekend, but it took too long and had be be aborted.
In the meantime, the aborted PVE migration has been erased from the FreeNAS array, which increases the free drive space from 20 GB to about 300 GB. This should provide more headroom, which will hopefully result in a (nominal) improvement in login times. The only thing users can do is delete unnecessary files to make both individual profiles load more quickly, and reduce the overall disk load. This will also allow the migration to happen more quickly.
We understand this is frustrating, and we are working to correct the problem. It wasn't planned to be a long-term situation, and we're trying to progress to the final configuration (all volumes on the SAN) as quickly as possible.
In the meantime, the aborted PVE migration has been erased from the FreeNAS array, which increases the free drive space from 20 GB to about 300 GB. This should provide more headroom, which will hopefully result in a (nominal) improvement in login times. The only thing users can do is delete unnecessary files to make both individual profiles load more quickly, and reduce the overall disk load. This will also allow the migration to happen more quickly.
We understand this is frustrating, and we are working to correct the problem. It wasn't planned to be a long-term situation, and we're trying to progress to the final configuration (all volumes on the SAN) as quickly as possible.
Sunday, January 10, 2010
Update [Sun., 2010-01-10, 21:55] Internet connection issues resolved
As of 9:55 PM Sunday, the district's Internet connection problems of the weekend seem to be resolved. The bottleneck seems to have been in the network packetshaper/traffic manager. It's supposed to throttle some traffic, but not all of it. (Sheesh!)
Internet access speed appears to be back to normal instead of the horribly slow speeds of the weekend. How bad was it? About as bad as the Packers' first quarter offense. (Thank you, I'll be here all night. Wait- no I won't. I'm going home now.)
Internet access speed appears to be back to normal instead of the horribly slow speeds of the weekend. How bad was it? About as bad as the Packers' first quarter offense. (Thank you, I'll be here all night. Wait- no I won't. I'm going home now.)
Tuesday, January 5, 2010
Server Maintenance Schedule
Ongoing Server maintenance outages for Oregon SD:
Friday, January 15: PVE server migration beginning at 7:00 p.m.
UPDATE: PVE Server migration phase1 complete @ 9:30 a.m., Jan 16. Be advised that the server may be restarted at any time Saturday and will be shut down again Saturday afternoon for phase 2 moving of datastore.
Saturday and Sunday, January 16 - 17: Servers PVE and PANTHER will be shut down for indeterminate amount of time for move to faster (and permanent) disk storage.
UPDATE: PVE Server migration phase1 complete @ 9:30 a.m., Jan 16. Be advised that the server may be restarted at any time Saturday and will be shut down again Saturday afternoon for phase 2 moving of datastore.
Saturday and Sunday, January 16 - 17: Servers PVE and PANTHER will be shut down for indeterminate amount of time for move to faster (and permanent) disk storage.
Subscribe to:
Comments (Atom)
